Introduction to two-factor authentication (2FA)
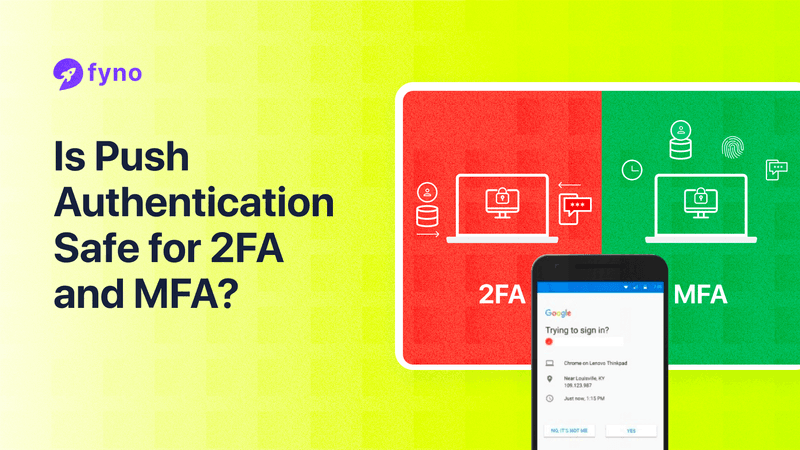
What is two-factor authentication, and why is it used?
Two-factor authentication (2FA) is a process in which two different types of authentication are required to validate your identity and grant access to your account. The first factor is typically your password, while the second factor can vary in complexity.
It can be a One-Time Password (OTP) sent to your mobile phone or email, or a code generated by an authenticator app linked to your account. By adding this additional layer of authentication beyond just a password, 2FA significantly enhances the security of your account.
Benefits of implementing two-factor authentication
Strengthened security: 2FA adds an extra layer of protection, significantly reducing the risk of unauthorized account access.
Mitigation of data breaches: 2FA minimizes the impact of data breaches by preventing account takeovers, even if passwords are compromised.
Enhanced account protection: 2FA makes it more challenging for attackers to gain control of user accounts, even with stolen login credentials.
Compliance with standards: Implementing 2FA helps organizations meet industry security standards and regulations, such as PCI DSS or HIPAA.
Increased user trust: Deploying 2FA demonstrates a commitment to account security, increasing user confidence and loyalty.
Understanding authentication factors
What are authentication factors?
Authentication factors are various 2FA methods that are used to verify a user's identity. Here are some of the most commonly used authentication factors.
Types of two-factor authentication products
- SMS authentication: Uses text messages to send verification codes to your registered mobile number.
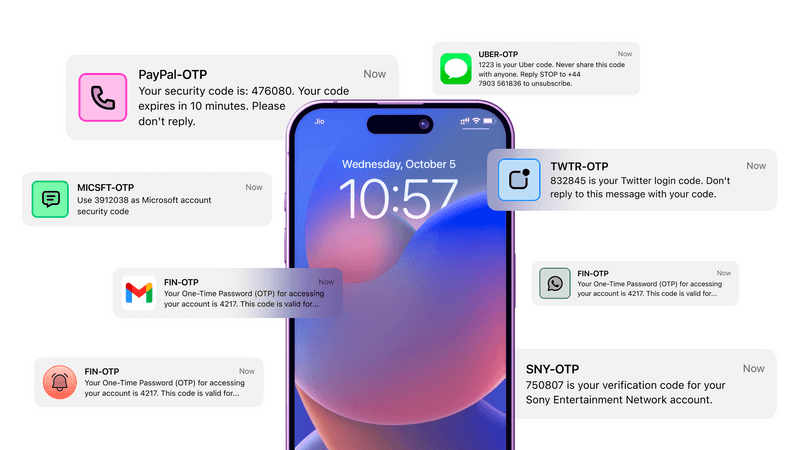
- Email verification: Sends verification links or codes to your registered email address.
- Authenticator apps: Generates time-based one-time passwords (TOTP) that keeps changing every 30–60 seconds. Some widely used Authenticator apps include Authy, Microsoft Authenticator, 2FAS, etc.
- Biometric authentication: Uses fingerprints, facial recognition, or other biometric information to verify the identity. This type of authentication is used for banking operations, verifying your identity to register or renew government documents, getting new mobile numbers, etc.
- Hardware tokens: Physical USB-based authentication devices like Yubi key are used to verify identity.

- Push notifications: Sends a prompt to a user's device for approval. This method is commonly used by apps like Gmail, Telegram, and Microsoft Outlook.
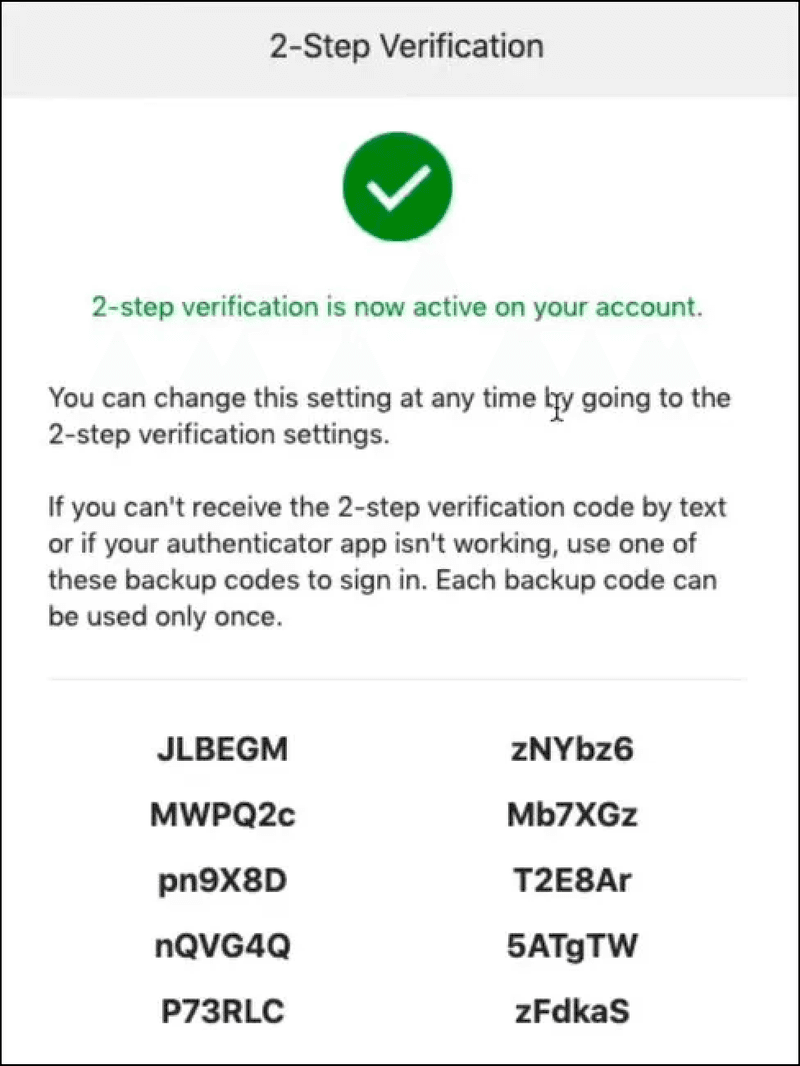
- Backup codes: Pre-generated codes used as a backup method. A lot of apps use this method as a backup if none of your authentication methods work. The use of backup codes is highly common among privacy-focused apps, apps that come with E2E (End-to-end encryption), and crypto trading platforms.
Now that we’ve seen all the authentication methods, let’s zoom in on push authentication and how it protects users.
How push authentication works
What is push authentication?
Push Authentication is a method where a notification is sent to a user's device, prompting them to approve or deny an authentication request.
How does push authentication work?
Step 1: A User enters their username and password to log into their account.
Step 2: Once the password is validated, a push notification is sent to the user's registered device.
Step 3: User approves the login attempt by pressing the action button in the notification.
Step 4: Once the user response is validated, the user is granted access to their account
Advantages and disadvantages of push authentication
Advantages
- Convenience: Easy for users to approve or deny login attempts with a single tap.
- Enhanced security: Reduces the risk of phishing attacks compared to SMS or email.
- Seamless integration: Easily integrates with existing security systems and applications.
Disadvantages
- Vulnerabilities and risks: Susceptible to certain types of attacks, such as MFA fatigue.
- Potential for MFA fatigue attacks: Users may be subjected to MFA fatigue attacks where they get repeated authentication requests on their device, leading to accidental approvals.
Security of push authentication
Is push authentication secure?
Push Authentication based 2FA is generally secure, but must be implemented in the right away to avoid vulnerabilities.
Preventing MFA push notification security flaws
- Limit authentication requests to prevent fatigue attacks: Attackers bombard users with repeated push notifications, hoping they will approve one out of frustration. You can prevent this by setting a threshold for the number of push notifications that can be sent for authentication purposes. If the user reaches the threshold, you can ask the user to use another form of authentication to access their account.
- Prevent MFA attacks with number matching and additional Context: Require users to enter a number displayed on the login screen or provide additional context about the login attempt. This is common while using Google and Microsoft apps.
- Show application name and enable geographical location for MFA: Display the name of the application and location of the login, attempt to help users identify suspicious activity.
Comparing push authentication with other 2FA methods
2FA vs. TOTP (Time-Based One-Time Password)
TOTP generates a time-sensitive code that the user must enter, while push authentication requires a simple approval, making it more user-friendly.
Push-based authentication vs. Other 2FA methods
Push-based authentication offers greater convenience, while matching the security impact delivered by SMS and email-based authentication. But, it may be less secure when compared to hardware tokens and biometric methods if not properly implemented.
Use cases and best practices for push authentication
Industries benefiting from push authentication
- BFSI (Banking, Financial Services, and Insurance): Push authentication adds another layer of security for account access, financial transactions, and user details updation.
- Logistics and high-volume customer communication sectors: In these cases, push notification ensures secure access to sensitive data without paving way for unauthorized access.
Best practices for implementing push authentication
- Educate users about fatigue attacks: Inform users about the importance of not approving suspicious requests.
- Use number matching: Add an extra layer of verification by requiring users to match numbers.
- Monitor and analyze: Continuously monitor authentication attempts and analyze for unusual patterns.
Future of authentication
Trends and innovations in authentication methods
The future of authentication is moving towards more secure and user-friendly methods, including passwordless authentication, location-based authentication, and authentication based on user behavior and patterns. While a lot of this is not being used widely, but we’ll see a lot of these over the next couple of years.
How Fyno can help?
With Fyno, you can seamlessly integrate your current push notification platforms like Google FCM, OneSignal, or Apple’s APN and set workflows to trigger them for various scenarios including sending notifications to authenticate account access. The advantage of using Fyno is you can manage the content, workflow, and the integration — all from one place.
Secure your user data with push authentication
Push authentication has emerged as a secure and user-friendly method for implementing two-factor authentication (2FA).
However, proper implementation is crucial to mitigate potential vulnerabilities, such as MFA fatigue attacks. Organizations can ensure a robust push authentication system by following best practices like limiting authentication requests, using number matching, and providing additional context.
To ease the time and effort taken to set up push authentication, you can use Fyno.io that offers a comprehensive solution for integrating push authentication into your applications and services. This allows seamless management of push notification workflows, content, and integrations from a single platform. By leveraging Fyno’s expertise, organizations can enhance their authentication process, protect user accounts, and provide a smooth user experience.
FAQs
1. What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a security process requiring two different methods to verify your identity, typically a password and a second factor like an OTP or biometric information.
2. What are the benefits of implementing 2FA?
Benefits include strengthened security, mitigation of data breaches, enhanced account protection, compliance with industry standards, and increased user trust.
3. What are authentication factors in 2FA?
Authentication factors include SMS authentication, email verification, authenticator apps, biometric authentication, hardware tokens, push notifications, and backup codes.
4. What is push authentication?
Push authentication sends a notification to a user's device, prompting them to approve or deny an authentication request.
5. How does push authentication work?
After entering a username and password, a push notification is sent to the user's device. The user approves the login attempt, and access is granted once validated.
6. Is push authentication secure?
Push authentication is generally secure but must be implemented properly to avoid vulnerabilities, such as limiting authentication requests and using number matching.
7. How can organizations prevent MFA fatigue attacks?
Organizations can limit authentication requests, use number matching, and provide additional context about login attempts to prevent fatigue attacks.
8. How does push authentication compare with other 2FA methods?
Push-based authentication is more user-friendly than TOTP and matches the security impact of SMS and email-based methods but may be less secure than hardware tokens and biometrics if not properly implemented.