What is SMS phishing (smishing)?
Smishing, a blend of “SMS” and “phishing,” refers to fraudulent attempts to obtain sensitive information through text messages. These smishing attacks often lure victims by pretending to be legitimate organizations. Attackers send deceptive SMS messages that prompt recipients to reveal personal information or click malicious links. Smishing is similar to voice phishing, where cybercriminals use phone calls to impersonate reputable entities like banks or customer service representatives to deceive individuals.
For example, you might receive a text message from what appears to be your bank asking you to verify your account information. This tactic is a common method to steal sensitive data, such as login credentials and financial information.

The difference between phishing and smishing
Phishing generally involves fraudulent emails, while smishing specifically targets mobile phones through SMS messages. Both phishing and smishing aim to deceive individuals into divulging sensitive information. However, smishing leverages the immediacy and perceived trustworthiness of text messages. Unlike emails, SMS messages are often read quickly, making recipients more susceptible to scams.
While smishing uses SMS, other phishing methods like vishing use phone calls to deceive individuals.
For instance, a smishing message might appear as a notification from a delivery service, prompting you to click a link to reschedule a delivery. This will ultimately lead to a fake website designed to steal your information.
This understanding of smishing is crucial for protecting your sensitive information from sophisticated social engineering attacks. Always verify the authenticity of SMS messages, especially those requesting personal or financial details. Awareness and caution are key to preventing smishing attacks and safeguarding your data.
How smishing works and spreads
1. How smishing attacks are delivered
Smishing attacks are delivered through fraudulent SMS messages designed to trick recipients into revealing sensitive information. These messages often contain malicious links that direct users to fake websites where they are prompted to enter personal or financial information. The attackers exploit SMS vulnerabilities to make these messages appear legitimate, often mimicking trusted organizations. Users must be cautious, especially when receiving unexpected messages. Businesses must also consider compliance with data protection regulations when implementing SMS authentication to enhance SMS security.
Smishing messages can also include deceptive text messages that claim to be from financial institutions or government agencies. These messages typically urge recipients to act immediately, such as verifying their bank accounts or logging into their online accounts. Fraudsters manipulate victims into providing sensitive data without verifying the message’s source by creating a sense of urgency.
2. Role of text messages in smishing attacks
Text messages play a critical role in phishing attacks, serving as the primary medium for delivering fraudulent content. SMS messages are particularly effective for phishing because they are perceived as more personal and trustworthy than emails. This trust makes it easier for attackers to deceive recipients into clicking on malicious links or providing sensitive information.
Fraudulent SMS messages often use social engineering tactics to exploit human psychology. For example, a smishing message might pretend to be a notification about a package delivery or a security alert from a bank. These messages can contain a verification code or a request for login credentials, aiming to capture sensitive information.
3. How fraudsters obtain mobile numbers
Fraudsters obtain mobile numbers through various means, often involving data breaches and social engineering. One common method is phishing attacks, where attackers trick individuals into revealing their phone numbers. Once obtained, these numbers are used to target victims with personalized messages in smishing attacks.
Another way fraudsters gather mobile numbers is by purchasing lists from data brokers, including phone numbers collected from various sources, including social media and online transactions.
Additionally, fraudsters may use automated tools to generate and test phone numbers. This brute force attack technique involves sending smishing messages to many randomly generated numbers, hoping that some will be active. Protecting personal phone numbers and being cautious about sharing them online can help reduce the risk of falling victim to smishing attacks.
The risks of smishing attacks
Identity theft and exposure of sensitive data: Smishing attacks, a type of SMS phishing, can cause severe identity theft. Attackers use deceptive text messages to access sensitive information, including personal details, login credentials, and financial data.
For instance, in 2022, 1.3 million U.S. identity theft cases were linked to smishing. Revealing personal information through these fraudulent messages puts individuals at high risk.
Financial consequences of smishing attacks: Smishing attacks can have devastating financial impacts, including unauthorized transactions and credit card fraud. Malicious links in smishing messages trick victims into divulging sensitive financial information.
For example, in 2021, smishing attacks cost Americans over $50 million. Financial institutions and legitimate organizations constantly warn customers about the dangers of SMS phishing.
Types of smishing attacks
COVID-19 smishing: COVID-19 smishing attacks surged during the pandemic, exploiting public fear with phishing SMS messages about vaccines or financial aid. These messages often contain malicious links that steal sensitive data like login credentials or personal details when clicked.
Financial services smishing: Financial services smishing targets bank customers with phishing SMS messages that appear to come from legitimate organizations. These messages often claim an urgent issue with the recipient's bank account, tricking them into revealing personal or financial information.
Gift smishing: Gift smishing lures recipients with promises of free gifts or prizes in text messages from seemingly legitimate brands. Clicking on these links can lead to fake websites that steal sensitive information, such as credit card details.
Examples of smishing attacks
1. Bank fraud messages: One common smishing attack involves receiving a message that appears to be from a bank warning about suspicious activity on your account. The message urges you to click on a link to verify your account information. When victims click the link, they are directed to a fake website where they can steal their login credentials and other sensitive information.
2. Package delivery scams: Attackers often send text messages claiming to be from a delivery service, stating there's an issue with a package delivery. The message includes a link to a fake website where victims are asked to enter personal information to reschedule the delivery. This information can then be used for identity theft or other malicious purposes.
3. Government agency impersonations: Some smishing attacks involve messages that appear to be from government agencies, such as the IRS or local authorities. Unless the recipient clicks a link or provides sensitive information, these messages may threaten legal action. The goal is to scare victims into divulging personal details or making immediate payments.
4. Tech support scams: Victims receive messages claiming a problem with their device or software. The message includes a link to a fake tech support site or a phone number to call. Once contact is made, the attacker may install malware on the victim's device or charge for unnecessary services.
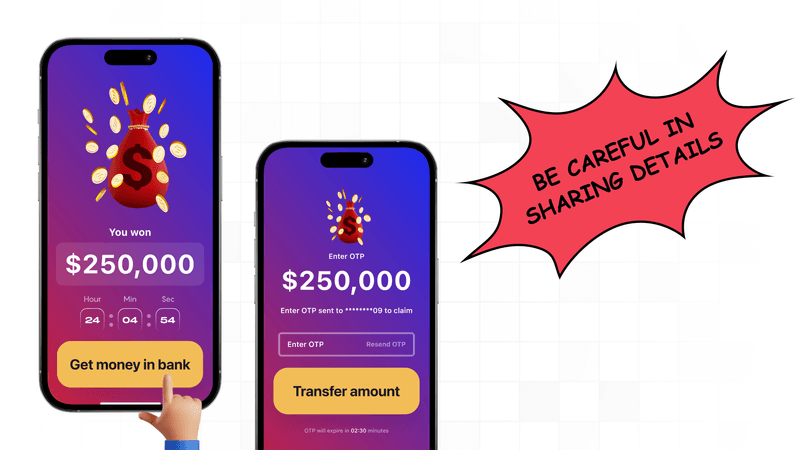
5. Lottery and prize scams: Attackers send messages informing recipients that they've won a prize or lottery. Victims are asked to provide personal information or pay a fee to claim their winnings. This data is then used for fraudulent activities or identity theft.
Common smishing scams
1. Financial institution scams: These scams trick recipients into providing sensitive data by pretending to be from banks or financial services. The messages often create a sense of urgency, pushing victims to act quickly without verifying the source.
2. Social media phishing: Attackers use text messages to direct victims to fake social media login pages. Once the victim enters their credentials, the attackers gain access to their accounts, which can be used for further fraudulent activities or to send more phishing messages.
3. Account verification scams: Victims receive messages claiming an issue with one of their online accounts (e.g., email, shopping sites). The message includes a link to a fake login page to steal their credentials.
4. Subscription renewal scams: Attackers send messages saying that a subscription (such as for streaming services) is about to expire. The message prompts victims to click a link to renew the subscription, leading to a phishing site where they enter their payment information.
5. Emergency and disaster relief scams: During natural disasters or emergencies, scammers send messages pretending to be from relief organizations, asking for donations. These messages often contain links to fake websites that collect personal and financial information.
Identifying and preventing smishing attacks
Characteristics of smishing messages
Smishing messages often seem legitimate, tricking users into revealing sensitive information. These messages typically include:
Urgent language: Phrases like "immediate action required" or "urgent update" are common.
Suspicious links: Links to websites that look legitimate but are actually fake.
Requests for sensitive data: Demands personal information, such as login credentials or credit card details.
Smishing attacks manipulate victims by using their trust in SMS messages. It's crucial to recognize these characteristics to avoid falling for such scams.
Red flags to watch out for in text messages
When evaluating text messages for potential smishing, watch out for:
Unsolicited messages: Messages from unknown numbers or unexpected sources.
Grammar and spelling errors: Legitimate organizations usually have well-crafted messages.
Personal or financial information requests: Be wary if asked to provide sensitive information.
Unverified links: Hover over links to check their actual destination before clicking.
Recognizing these red flags can help protect against smishing attacks, which aim to gather sensitive data through deceptive text messages.
Best practices for protecting yourself from smishing
To safeguard against smishing, follow these best practices:
Verify the sender: Confirm the sender's identity before responding to any SMS message.
Avoid clicking on links: Refrain from clicking on links in unsolicited messages.
Use Multi-Factor Authentication (MFA): Enhance security by enabling MFA on all online accounts.
Educate yourself: Stay informed about the latest smishing tactics and how to spot them.
Report suspicious messages: Report any suspicious SMS messages to your mobile carrier or relevant authorities.
By adopting these practices, you can significantly reduce the risk of falling victim to smishing scams.
What to do if you become a victim of smishing
Smishing attacks can be alarming, especially when sensitive information is lost. If you become a victim, prompt action is crucial. This section will guide you through immediate steps and reporting processes to protect your identity and secure your data.
Immediate steps to take after falling victim to smishing
Cease communication: Stop interacting with spam messages immediately. Avoid clicking any links or providing further information.
Change passwords: Update the passwords for your online accounts, particularly those related to banking, email, and social media. Use strong, unique passwords and consider enabling multi-factor authentication.
Notify your bank: Contact your bank or financial institution immediately. Inform them about the smishing attack to safeguard your accounts from unauthorized transactions.
Run a security scan: Use anti-malware software to scan your mobile device for any malicious software that might have been installed through the smishing attack.
Monitor financial accounts: Regularly check your bank statements and credit reports for suspicious activity. Early detection can help mitigate potential financial loss.
How to report smishing attacks and protect your identity
Report to authorities: Inform local law enforcement agencies and provide them with all the details of the smishing attack. This helps in tracking and preventing further scams.
Notify your carrier: Report the smishing message to your mobile carrier. They can take measures to block such messages and enhance your SMS security.
Contact the FTC: In the United States, report the smishing attack to the Federal Trade Commission (FTC). The FTC provides resources and guidance on dealing with identity theft and fraudulent activities.
Alert your network: Inform friends, family, and colleagues about the smishing attack. This will spread awareness and help them avoid similar scams.
Use identity protection services: Consider subscribing to identity protection services. These services monitor your personal information and alert you to potential identity theft.
Staying safe from smishing and other phishing attacks
Smishing attacks often involve fraudulent SMS messages that trick recipients into revealing personal or financial information. Understanding the tactics used in these attacks is the first step in preventing them.
The importance of awareness and education in preventing smishing attacks
Educate yourself and your team: Knowledge is the best defence against smishing. Regularly update your team about the latest smishing tactics and SMS phishing attacks. Awareness training helps in recognizing and avoiding malicious links in deceptive text messages.
Recognize red flags: Smishing messages often urge immediate action or create urgency. Learning to identify these cues can prevent unauthorized transactions and data theft. Always verify the legitimacy of any request for sensitive data.
Promote security awareness training: Implementing comprehensive training programs can drastically reduce the risk of smishing attacks. Such training should cover handling SMS vulnerabilities and not divulging sensitive information via text.
Tools and resources for staying informed
Use anti-malware software: Install anti-malware software on mobile devices to detect and block phishing SMS attempts. This software can provide an additional layer of security against smishing scams and malicious links.
Subscribe to security updates: Stay updated with the latest security threats and solutions by subscribing to reputable cybersecurity newsletters and alerts. Organizations can use these resources to inform employees about new smishing techniques and SMS security issues.
Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it harder for attackers to access sensitive accounts even if login credentials are compromised. This is crucial for protecting online accounts and financial transactions.
Regular security audits: Conduct regular security audits to identify and address SMS vulnerabilities within your organization. Audits help ensure that your systems and processes are up-to-date and capable of resisting smishing attacks.
Understanding the methods attackers use and implementing robust security measures are essential in protecting sensitive data and maintaining SMS security.
How Fyno can help prevent and mitigate smishing attacks
Fyno offers a robust multi-channel communication platform designed to enhance security and prevent smishing attacks. By integrating all communication channels—SMS, email, push notifications, and more—into a single API, Fyno streamlines communication management and reduces the complexity of monitoring multiple channels individually.
Unified API integration: Fyno provides a single API to manage all communication channels, simplifying the integration process and reducing the risk of vulnerabilities that can be exploited in smishing attacks. This unified approach ensures consistent security protocols across all channels.
Intelligent routing and automation: Fyno's intelligent routing capabilities ensure messages are delivered through the most secure and reliable channels. Automated workflows help detect and block suspicious activities in real-time.
Centralized management: By centralizing communication management, Fyno enables comprehensive monitoring and quick response to potential threats, ensuring timely intervention and mitigation of smishing attacks.
Enhanced security features for regulated industries
For industries such as banking and finance, where regulatory compliance is critical, Fyno offers enhanced security features tailored to meet these stringent requirements.
Data masking and hashing: Fyno ensures sensitive information is protected through data masking and hashing, making it difficult for attackers to access or misuse personal or financial information.
Access controls: Implementing strict access controls, Fyno ensures that only authorized personnel can access sensitive data, reducing the risk of internal threats.
Compliance with regulations: Fyno adheres to global privacy and security standards, helping businesses comply with data protection regulations such as GDPR and SOC2. This compliance reduces the risk of hefty fines and reputational damage due to data breaches.
Real-time monitoring and alerts for suspicious activity
Fyno provides real-time monitoring and alerts to quickly identify and respond to suspicious activities, which is crucial in preventing and mitigating smishing attacks.
Anomaly detection: Fyno’s platform includes advanced anomaly detection capabilities to identify unusual patterns in communication traffic that may indicate a smishing attack. This proactive approach helps in early detection and prevention of potential threats.
Real-time alerts: The system generates real-time alerts for any suspicious activity, enabling swift action to mitigate threats. These alerts ensure that security teams are immediately notified of potential smishing attempts.
Detailed reporting: Fyno provides comprehensive reports and analytics on communication activities, allowing businesses to track and analyze trends, identify vulnerabilities, and improve their security posture.
FAQs
1. What is SMS phishing (smishing)?
Smishing is a type of phishing attack that uses SMS messages to trick recipients into revealing sensitive information.
2. How can one identify a smishing message?
Look for urgent language, suspicious links, and requests for sensitive data in unsolicited messages.
3. What should one do if they receive a suspicious SMS?
Do not click on any links, verify the sender, and report the message to your mobile carrier or relevant authorities.
4. How can one protect themselves from smishing attacks?
Use multi-factor authentication, avoid clicking on links in unsolicited messages, and stay informed about the latest smishing tactics.
5. What are the common types of smishing attacks?
Common types include financial institution scams, social media phishing, and package delivery scams.
6. What immediate steps should one take if one falls victim to smishing?
Cease communication with the sender, change your passwords, notify your bank, and run a security scan on your device.
7. How do fraudsters obtain mobile numbers for smishing?
Fraudsters obtain mobile numbers through data breaches, social engineering, and purchasing lists from data brokers.