What is communication security (COMSEC)?
Communication security, often known as COMSEC, involves protecting communication channels from unauthorised access and ensuring the confidentiality, integrity, and authenticity of transmitted information. It is crucial to protect communications traffic to ensure data privacy and security.
Businesses rely on secure communication to protect sensitive data, maintain privacy, and ensure the smooth operation of their activities. Effective communication security measures prevent cyber threats and data breaches, making it a critical aspect of modern business operations.
Why is business communication security important?
Communication security is vital for safeguarding business information against potential cyber threats. As businesses increasingly rely on digital communication, the risk of data breaches and cyber-attacks has risen.
Communication security problems stemming from historical vulnerabilities pose critical issues for organizations. The evolution of security measures like encryption and spread spectrum technologies has been essential in addressing these challenges.
Protecting communication channels helps maintain the confidentiality of sensitive business information, preventing unauthorised access and ensuring secure business operations.
1. Preventing security breaches and potential threats
Implementing robust communication security measures is essential for preventing security breaches. Attackers often hijack email accounts to obtain access to organization or client information, posing significant risks such as hacking, phishing, and data theft. By securing communication channels, companies can protect themselves from these threats, ensuring that their data remains safe and their operations uninterrupted.
2. Role of encryption in communication security
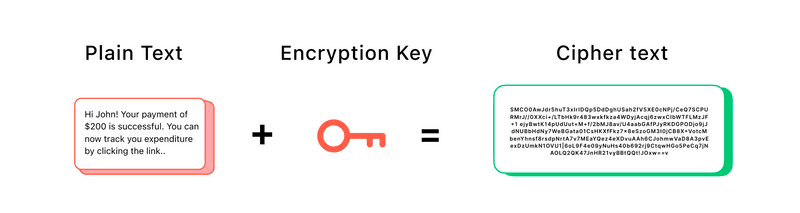
Encryption plays a crucial role in communication security by converting data into a coded format, making it unreadable to unauthorised users. Cryptographic security is a key component of measures to protect information, ensuring the authenticity and confidentiality of telecommunications. Businesses can use strong encryption methods to ensure that even if data is intercepted, it remains secure. Encryption is particularly important for protecting sensitive information such as financial data, customer details, and proprietary business information.
3. Ensuring data integrity and confidentiality
Ensuring data integrity and confidentiality is a core component of communication security. Businesses must implement measures to verify that data has not been altered during transmission and to deny unauthorized persons information derived from telecommunications. This is achieved through the use of secure protocols and encryption, which protect data from tampering and unauthorized access.
By focusing on these three aspects of communication security, businesses can safeguard their operations, protect sensitive information, and maintain the trust of their clients and partners.
Key risk points in email communication security
Attackers gaining access to email accounts: Unauthorised access to email accounts can lead to significant security breaches. Use strong passwords and enable multi-factor authentication to protect against password phishing and brute force attacks.
Transmission of malware and phishing attacks: Phishing and malware are common email threats. Educate employees to recognize phishing attempts and avoid suspicious links. According to Verizon, 94% of malware is delivered via email.
Unintentional data leaks: Data leaks can occur through misaddressed emails or wrong attachments. Implement data loss prevention (DLP) tools to monitor and protect data in transit.
Importance of email encryption: Encrypting emails ensures that only the intended recipient can read the content. A study by Symantec found that 40% of organizations use email encryption to enhance security.
Addressing these risks helps improve communication security and ensures safer email practices.
Physical security measures
Protecting physical infrastructure and devices
Importance of securing servers and communication systems: Securing servers and communications systems is vital to ensure business communication security (COMSEC). Physical threats can compromise sensitive data, leading to significant financial and reputational damage. Protecting these systems prevents unauthorised access and ensures the integrity of communications.
On-premise deployment for maximum safety: On-premise deployment of servers and communication systems enhances security by providing greater control over physical access. This method reduces the risk of data breaches and unauthorised interventions. Businesses can tailor security measures to meet their specific needs, ensuring a robust security communication framework.
Efficient alarm systems for swift response: Implementing efficient alarm systems is crucial for swift response to potential threats. These systems can detect unauthorized access or environmental hazards, alerting security personnel immediately. Quick responses can prevent or minimise damage, ensuring continuous communication security.
Securing data centres and servers
Restricting access to authorised personnel: Restricting access to data centres and servers to authorised personnel only is essential for maintaining security.
Implementing strict access control measures, such as ID verification and logging entry times, helps prevent unauthorized access and ensures that only trusted individuals handle sensitive information.
Use of surveillance cameras and biometric authentication: Surveillance cameras and biometric authentication enhance security by providing real-time monitoring and precise identification.
Surveillance cameras deter unauthorised access, while biometric systems, such as fingerprint or retina scanners, ensure that only verified personnel can access critical areas. This dual approach strengthens communication and security protocols.
Protection against natural disasters and power outages: Protecting data centres and servers from natural disasters and power outages is crucial for maintaining communication security. Implementing disaster recovery plans, such as backup power supplies and data redundancy systems, ensures that business operations continue seamlessly, even during emergencies.
According to a study by FEMA, 40% of businesses never reopen after a disaster, emphasising the importance of robust protection measures.
Implementing these physical security measures can significantly enhance the security of business communication systems, safeguarding sensitive information and ensuring uninterrupted operations.
Ensuring transmission security
Data encryption in transit
Vulnerability of data during transit: Data in transit is highly susceptible to interception and unauthorised access. This vulnerability arises because data is often transmitted over public or untrusted networks, where malicious actors can intercept it.
Importance of End-to-End (E2E) encryption: End-to-end (E2E) encryption plays a vital role in securing data during transit. This method ensures that data is encrypted from the time it leaves the sender's device until it reaches the intended recipient.
E2E encryption guarantees that data will remain unreadable and secure even if it is intercepted during transmission. According to a recent study, organizations implementing E2E encryption reduce the risk of data breaches by 30%.
Role of cryptographic keys in decryption: Cryptographic keys, which can be symmetric or asymmetric, are fundamental to the encryption and decryption process. They encrypt data before transmission and decrypt it upon receipt.
The National Security Agency (NSA) plays a crucial role in the development and utilization of cryptographic equipment and technologies.
Symmetric keys use the same key for both encryption and decryption, while asymmetric keys use a public and private key pair. The security of cryptographic keys is paramount; if a key is compromised, unauthorised parties can easily decrypt the encrypted data.
Regular key management practices, such as key rotation and secure key storage, are critical for maintaining the integrity of encrypted communications.
Secure protocols for data transmission
Use of HTTPS and SFTP for secure communication: HTTPS (Hypertext Transfer Protocol Secure) ensures that web communications are encrypted and secure, protecting against eavesdropping and man-in-the-middle attacks. SFTP (Secure File Transfer Protocol) provides a secure method for transferring files over a network
Both protocols utilize encryption to safeguard data during transmission, ensuring that sensitive information remains confidential. Implementing HTTPS and SFTP in business communications is a best practice for enhancing network security and protecting sensitive data.
Regular security audits to ensure protocol integrity: Conducting regular security audits is essential for maintaining the integrity of secure communication protocols. These audits help identify vulnerabilities and weaknesses in existing security measures, allowing organisations to address potential threats proactively.
A comprehensive security audit includes reviewing protocol configurations, checking for outdated software, and verifying that encryption standards are up-to-date.
Best practices for implementing communication security
Business communication security (COMSEC) is crucial for protecting sensitive information. Proper implementation ensures the integrity and confidentiality of communications within a business.
Effective COMSEC practices are essential to safeguard data against unauthorized access and breaches in today's digital age. The following best practices will help you implement robust communications security.
Importance of cryptography in communications security
Cryptography plays a vital role in securing business communications. It involves converting messages into indecipherable characters to protect them from unauthorized access. This process ensures that only intended recipients can read the communication, providing an additional layer of security.
Key components of a secure communication system include servers, encryption algorithms, and digital keys, which are essential for maintaining security and functionality. Digital keys are essential for encrypting and decrypting messages, enabling secure communication channels.
Protecting communications from unauthorized access: Protecting communications from unauthorized access is paramount in maintaining business security. Unauthorized access can lead to data breaches and loss of confidential information. Implementing strong cryptographic measures can prevent such incidents.
Conversion of messages into indecipherable characters: The conversion of messages into indecipherable characters is a fundamental aspect of cryptography. This process, known as encryption, ensures that sensitive information remains confidential during transmission. Encrypted messages are only accessible to those with the correct decryption keys.
Role of digital keys in encryption and decryption: Digital keys are crucial in the encryption and decryption process. These keys must be managed securely to maintain the integrity of the communication system. Regular updates and secure storage of digital keys are necessary to prevent unauthorised access.
Implementing encryption and decryption methods
Implementing effective encryption and decryption methods is essential for securing business communications. These methods protect data at rest and in transit, ensuring that sensitive information is always secure.
Secure communication protocols: Using secure communication protocols is fundamental to business communication security. Protocols like TLS (Transport Layer Security) provide encrypted communication channels, preventing unauthorised interception of data.
Encryption of data at rest and in transit: Encrypting data at rest and in transit ensures comprehensive protection of sensitive information. Data at rest encryption protects stored data, while data in transit encryption secures information as it moves across networks. Both are essential for a robust security strategy.
Key management infrastructure and regular audits: A strong key management infrastructure is critical for maintaining secure communications. This includes securely generating, distributing, storing, and rotating keys. Regular audits of the key management system help identify vulnerabilities and ensure compliance with security standards.
Implementing these best practices in business communication security can significantly reduce the risk of data breaches and unauthorized access. Businesses can safeguard their sensitive information by prioritizing cryptography, secure communication protocols, and robust key management.
Admin controls and regular audits
Managing access to sensitive information is crucial for communication security. Businesses must ensure that only authorized personnel can access critical data. Implementing role-based access controls helps limit exposure, and periodic reviews and updates of access permissions prevent unauthorized access.
Regularly inspecting employee access is vital to identifying unauthorized attempts and ensuring appropriate access levels, maintaining high security standards and protecting against potential breaches.
Regular security audits and risk assessments
Outsourcing audits to reliable third parties: Outsourcing security audits to reliable third-party organizations can provide an unbiased assessment of your communication security. These audits identify vulnerabilities and recommend improvements. Additionally, they ensure emissions security by preventing unauthorized interceptors from accessing telecommunications in an intelligible form. This practice is particularly beneficial for businesses lacking in-house security expertise.
Conducting surprise audits for unusual activity: Conducting surprise security audits can help detect unusual activities that regular audits might miss. These audits keep employees vigilant and ensure adherence to security protocols. Regular surprise audits contribute to a robust security environment by identifying and addressing issues promptly.
Identifying and addressing vulnerabilities
Implementing patches and updating software: Implementing patches and regularly updating software is essential to maintaining business communication security. Ensure all systems are up-to-date with the latest security patches to prevent vulnerabilities. This proactive approach minimizes the risk of cyber threats.
Conducting employee training to prevent breaches: Regular employee training sessions are crucial in preventing security breaches. Educate employees on best practices for communication and security, such as recognizing phishing attempts and safely handling sensitive information. Well-informed employees are a critical line of defence against security breaches.
Ensuring robust admin controls and regular audits significantly enhances business communication security. Implementing these best practices helps maintain a secure communication environment, protect sensitive information and reduce the risk of security breaches.
Educating Employees on Communication Security
Internal training on communication security best practices
Importance of following secure communication procedures: Businesses must ensure employees follow secure communication procedures. This practice protects sensitive data and maintains the integrity of business operations. According to a report by IBM, human error is a major factor in 95% of cybersecurity breaches. By educating employees, businesses can significantly reduce the risk of such incidents.
Regular training sessions to strengthen security: Conducting regular training sessions helps keep security protocols fresh in employees' minds. Frequent training ensures that employees are updated on the latest security practices and potential threats. The National Cyber Security Centre recommends training at least every six months to keep security awareness high.
Importance of cybersecurity while working remotely: With the rise of remote work, cybersecurity has become more critical than ever. Employees need to be aware of secure communication practices while working from home. Using secure networks, avoiding public Wi-Fi, and employing VPNs are essential practices. Global Workplace Analytics states remote work has grown by 173% since 2005, making cybersecurity training imperative.
Careful third-party use and vendor management
Transparency in metadata collection and use: When working with third-party vendors, transparency in metadata collection and use is crucial. Businesses should ensure vendors adhere to the same security standards and clearly communicate how data is collected, used, and stored. The General Data Protection Regulation (GDPR) emphasizes the importance of transparency in data practices.
Benefits of open-source messaging solutions: Open-source messaging solutions can offer enhanced security benefits. These solutions allow businesses to review and verify the code, ensuring no vulnerabilities exist. They often have robust communities that regularly update and patch security issues. For example, Signal is an open-source messaging app known for its strong encryption and security features.
Incorporating these practices helps businesses improve their communication security. Educating employees and managing third-party use effectively can enhance overall security, ensuring that business communication remains protected.
Ongoing monitoring and detection of attacks
Effective business communication security requires continuous vigilance. Ongoing monitoring and detection of attacks are crucial to protecting sensitive information and ensuring uninterrupted operations.
Continuous monitoring and intrusion detection
Implementation of Intrusion Detection and Prevention Systems (IDPS): IDPS monitor network traffic for suspicious activities, blocking potential threats. This significantly reduces data breach risks, which average $3.86 million per incident according to IBM, by providing real-time alerts and automatic threat mitigation.
Conducting regular security audits: Regular security audits identify vulnerabilities and ensure security measures are current. For instance, in the BFSI sector, they prevent unauthorized access to financial data. A 2021 Deloitte report states that 67% of organizations conduct regular audits to enhance security posture.
Training employees to identify and report suspicious activity: Training employees to recognize and report suspicious activities allows businesses to act quickly against threats. This is vital in industries like logistics, where communication security is key. Studies show that 90% of cyber attacks result from human error, highlighting the need for effective training programs.
Incorporating continuous monitoring and intrusion detection practices enhances communication security and fortifies overall business resilience. These measures ensure that any attempts to breach security are swiftly detected and mitigated, protecting sensitive business communications and data.
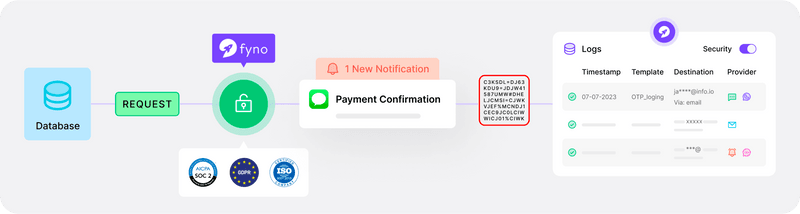
Fyno's approach to communication security
In today's digital landscape, ensuring secure business communications is paramount. Fyno offers robust solutions that protect multi-channel communications tailored to meet industry-specific needs, regulatory compliance, advanced encryption, and continuous monitoring.
Multi-channel security
Ensuring security across multiple communication channels is crucial for protecting sensitive data. For example, if you use Meta to send WhatsApp messages and Amazon SES to send emails, someone getting hold of the token can misuse it.
Fyno addresses this by encrypting all your credentials to ensure they are not compromised. This encryption safeguards your communication channels, preventing unauthorized access and ensuring secure data transmission.
Regulatory compliance support
Helping businesses meet compliance requirements is a fundamental aspect of communication security. Fyno supports compliance with standards such as ISO, SOC2 Type 2, and GDPR. Regular audits, security assessments, and updated protocols ensure adherence to these regulations, helping businesses avoid penalties and maintain customer trust.
Advanced encryption and security features
Fyno employs cutting-edge technology for secure communications, including:
Data hashing: All customer Personally Identifiable Information (PII) is hashed, ensuring that even Fyno’s systems do not have access to it.
Data masking: PII is hidden, further protecting sensitive information.
Alerts: Anomaly detection alerts businesses to potential security threats in real-time, allowing for immediate action.
Continuous monitoring and support
24/7 support and regular security updates are essential for maintaining robust communication security. We provide continuous monitoring to detect and mitigate security threats in real-time. Regular updates ensure that systems are protected against new vulnerabilities.
Conclusion
Ensuring business communication security is essential in today's digital landscape. By understanding COMSEC and following best practices, businesses can protect their sensitive information, maintain compliance, and ensure smooth operations. Implementing robust security in communication strategies will help mitigate risks and safeguard business communications against potential threats.
FAQ
What is Communication Security (COMSEC)?
COMSEC, often known as communication security, involves protecting communication channels from unauthorized access and ensuring the confidentiality, integrity, and authenticity of transmitted information.
Why is business communication security important?
Business communication security is vital for safeguarding sensitive data against cyber threats and ensuring secure and uninterrupted operations.
What role does encryption play in communication security?
Encryption converts data into a coded format, making it unreadable to unauthorized users, thus protecting sensitive information during transmission.
How can businesses prevent security breaches in communication?
Implementing robust communication security measures, such as encryption, secure protocols, and regular security audits, can help prevent security breaches.
What are the risks associated with email communication?
Risks in email communication include unauthorized access, malware, phishing attacks, and unintentional data leaks, all of which can be mitigated with strong security practices.
Why is end-to-end encryption important for data transmission?
End-to-end encryption ensures that data remains encrypted from sender to recipient, protecting it from unauthorized access during transmission.
What are some best practices for maintaining communication security?
Best practices include using strong encryption methods, implementing secure communication protocols, conducting regular security audits, and educating employees on security procedures.