What is SMS authentication?
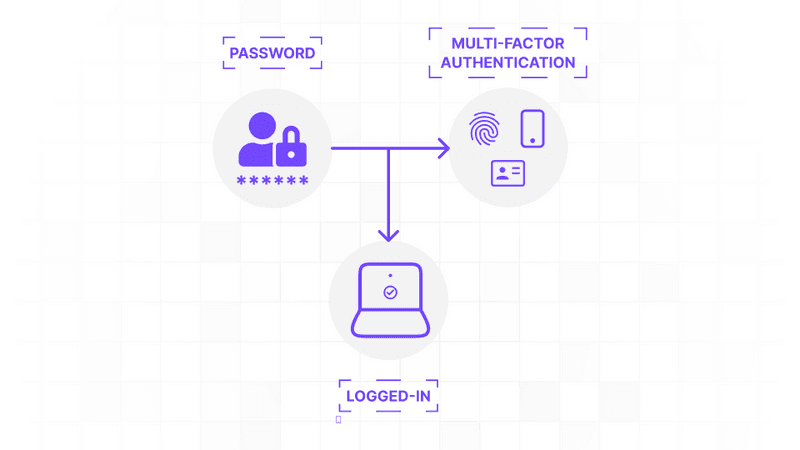
SMS Authentication is a security process where a user receives a unique code via a text message to verify their identity. This method is part of multi-factor authentication (MFA) and adds an extra layer of security to online accounts.
It requires both a password and a code sent to a mobile phone, preventing unauthorised access even if a password is compromised.

How SMS authentication works using SMS codes
SMS authentication is a widely used method for securing online accounts. It involves sending an SMS authentication code to the user's phone when they attempt to log in. This code is typically a one-time password (OTP) that the user must enter on the website or app to gain access.
Steps for SMS authentication:
User log in with their username and password.
A unique SMS code is sent to their registered mobile phone.
User enters the SMS authentication code on the login page.
The system verifies the code, granting access if the code is correct.
This process adds an extra layer of security, ensuring that even if a hacker steals the user's password, they cannot log in without access to the user's mobile phone.
Types of One-Time Passwords (OTPs)
One-time passwords (OTPs) are crucial in SMS authentication, providing a temporary code for user verification. Different types of OTPs are used in authentication methods, each with unique features.
Types of OTPs:
Time-based OTPs (TOTP): These OTPs are generated based on the current time and are valid for a short duration, typically 30 seconds to 1 minute. They are used in many authentication apps.
Event-based OTPs (HOTP): These are generated based on a counter that increments each time an OTP is requested. They remain valid until used, providing flexibility in timing.
Biometric OTPs: In some advanced systems, OTPs are generated based on biometric data such as fingerprints or facial recognition, offering high security.
SMS-based OTPs: These are sent directly to the user's mobile phone via text message and are commonly used due to their simplicity and widespread mobile phone usage.
Each type of OTP enhances security by ensuring that the password can only be used once and within a specific context, reducing the risk of unauthorized access.
Benefits of SMS authentication
SMS authentication offers several advantages, making it a popular choice for securing access to online accounts and services. This method adds a layer of security, which is crucial for protecting sensitive customer data and preventing unauthorized access.
Additionally, SMS authentication is easy to use and widely understood by users, which increases the likelihood of adoption and successful implementation.
User-friendly and widely adopted
Ease of use: SMS authentication is straightforward, requiring users to receive and enter a code sent via text message. This simplicity makes it accessible to a broad range of users, including those who may not be tech-savvy.
Broad acceptance: Due to its simplicity, many organizations across various sectors, including BFSI and logistics, have adopted SMS authentication as a standard security measure. According to a study by Symantec, SMS-based two-factor authentication is used by over 76% of organizations globally.
Familiarity: Most users are already familiar with receiving and reading SMS messages, which reduces the learning curve and increases the likelihood of successful implementation and user compliance.
Easy to implement and integrate
Integration with existing systems: SMS authentication can be easily integrated into existing login systems without significant changes. It is compatible with various platforms and services, making it a flexible solution for enhancing security.
Developer-friendly: Many SMS API providers offer straightforward integration processes, allowing developers to add SMS authentication features with minimal effort.
Quick deployment: The setup process for SMS authentication is quick, allowing organizations to enhance their security measures promptly. This is particularly beneficial for companies needing to secure user accounts rapidly in response to emerging threats.
Cost-effective for small-scale implementations
Affordable solution: Implementing SMS authentication is relatively inexpensive compared to other multi-factor authentication methods. This makes it an attractive option for small businesses and startups that need robust security without breaking the bank.
No additional hardware required: Unlike hardware tokens or biometric systems, SMS authentication does not require users to purchase or maintain additional devices. Users only need their mobile phones, which they already possess.
Scalable: As businesses grow, SMS authentication can scale with them. Service providers typically offer flexible pricing models that accommodate the needs of both small-scale and large-scale implementations, ensuring that the solution remains cost-effective as the company expands.
Security concerns of SMS authentication
SMS authentication, while widely used, raises significant security concerns. One major issue is the vulnerability to SMS spoofing, SIM swapping, and social engineering attacks. These methods can compromise user accounts and lead to unauthorized access.
Additionally, the lack of encryption in SMS messages poses a risk to the confidentiality of the authentication process.
Vulnerabilities to SMS spoofing, SIM swapping, and social engineering
SMS spoofing: Attackers can manipulate the sender information of a text message to appear as if it is from a trusted source. This can lead to users unknowingly sharing sensitive information.
SIM swapping: This technique involves transferring a victim's phone number to a new SIM card controlled by the attacker. Once the transfer is complete, the attacker can intercept SMS messages, including authentication codes.
Social engineering: Attackers often use social engineering tactics to trick users into revealing their authentication codes or other personal information. This can be done through phishing attacks, where users are directed to fake websites.
Limited security: SMS messages are not encrypted
SMS messages are not encrypted by default. This lack of encryption means that the information can be read in plain text if the messages are intercepted. This poses a significant risk for SMS authentication, especially when dealing with sensitive data such as login credentials or one-time passwords (OTP).
Comparison to other authentication methods for enhanced security
Authenticator apps: Unlike SMS, authenticator apps generate codes locally on the device and do not rely on network-based transmission, making them more secure against interception.
Public key cryptography: This method uses a pair of keys (public and private) to encrypt and decrypt data, providing a high level of security. It is widely used in securing online transactions and communications.
Biometric authentication: Using fingerprints, facial recognition, or voice recognition adds an extra layer of security that is difficult to replicate or steal.
Hardware tokens: These physical devices generate authentication codes and are considered highly secure since they are not connected to the internet and require physical possession.
Alternatives to SMS authentication
SMS authentication is a widely used method for securing online accounts. However, it has some vulnerabilities that have led many organizations to explore alternative authentication methods.
Here are some effective alternatives to SMS authentication:
Authenticator apps: Mobile authenticator apps generate time-based one-time passwords (TOTP) that provide a layer of security. These apps, like Google Authenticator and Authy, do not rely on cellular service, making them less susceptible to SIM swapping and other attacks.
FIDO2 (WebAuthn) and U2F security keys: These hardware-based authentication methods offer robust security. FIDO2 and U2F keys use public key cryptography to verify the user's identity without transmitting sensitive information over the network, significantly reducing the risk of phishing attacks.
Biometric authentication: Methods like fingerprint scans, facial recognition, and voice recognition provide enhanced security by verifying a unique physical characteristic of the user. Biometric data is difficult to replicate, offering strong protection against unauthorized access.
Email authentication: Sending a one-time password (OTP) or verification link to the user's email adds another layer of security. This method is useful when combined with other authentication factors for multi-factor authentication (MFA).
Security questions and answers: While not the most secure method, combining security questions with other factors can improve overall security. It is essential to use questions with answers that are hard to guess or find through social engineering.
Push notifications: Some services use push notifications sent to the user’s mobile device for authentication. This method can be more secure than SMS as it involves app-specific notifications.
Smart cards: Used primarily in enterprise settings, smart cards can store authentication credentials securely and require a physical card reader for access.
Behavioral Biometrics: This method analyzes user behaviour, such as typing patterns or mouse movements, to verify identity. It is often used as an additional layer of security.
FIDO2 (WebAuthn) and U2F security keys for multi-factor authentication (MFA)
FIDO2 (WebAuthn) and U2F security keys are among the most secure alternatives to SMS authentication. They use public key cryptography to authenticate users without transmitting sensitive information over the network.
Enhanced security: These keys resist phishing and man-in-the-middle attacks because they do not share secret data with the online service.
Ease of use: Users can simply insert their key into a USB port or connect via NFC, providing a seamless and quick authentication process.
Widely supported: Many online services, including Google, Microsoft, and Dropbox, support FIDO2 and U2F keys, making it easier for users to secure multiple accounts with a single key.
Case study: A major financial institution reported a 99% reduction in account takeovers after implementing FIDO2 security keys for its customers.
Mobile authenticator apps and TOTP passcodes for added security
Mobile authenticator apps, such as Google Authenticator and Authy, provide time-based one-time passwords (TOTP) that offer enhanced security compared to SMS authentication.
Offline access: These apps generate codes even when the user's phone is offline, making them reliable in areas with poor cellular coverage.
Reduced vulnerability: Since TOTP codes do not rely on SMS, they are less vulnerable to SIM swapping and other forms of interception.
Integration: Many services, including banking and logistics companies, support authenticator apps, allowing seamless integration for users across various platforms.
User example: A logistics company found that using authenticator apps reduced unauthorized access attempts by 80%, highlighting the effectiveness of this method.
Biometric authentication and other methods for enhanced security
Biometric authentication methods offer a high level of security by using unique physical characteristics of the user.
Fingerprint scanning: Widely used in smartphones and some laptops, fingerprint scanning provides quick and secure access to accounts and devices.
Facial recognition: Services like Apple's Face ID offer a convenient and secure way to authenticate users. Facial recognition technology is becoming more accurate and widely adopted.
Voice recognition: Some services use voice recognition as an additional layer of security. This method can be particularly useful in call centres and customer service operations.
Case study: A bank implemented facial recognition for mobile app access, reducing unauthorized access attempts by 95%.
Implementing multi-factor authentication (MFA)
Multi-factor authentication (MFA) enhances security by requiring multiple verification methods before granting access. It often includes authenticating by SMS, where users receive a code on their mobile phones to verify their identity.
Best practices for choosing an authentication method
When selecting an authentication method, consider the following best practices:
Assess security needs: Determine the level of security required based on the sensitivity of the data. MFA, including SMS codes, provides a layer of protection.
User convenience: Ensure the method is user-friendly. Text message authentication is widely accepted due to its simplicity and accessibility.
Cost-effectiveness: Evaluate the cost of implementation and maintenance. It is cost-effective compared to other methods, such as biometric verification.
Compliance with standards: Choose methods that comply with industry standards and regulations to avoid legal issues.
scalability: Ensure the authentication method can scale with your business growth.
Importance of compliance and regulatory requirements
Adhering to compliance and regulatory requirements is essential for maintaining trust and avoiding legal repercussions.
Understand regulations: Familiarize yourself with relevant regulations in your industry.
Implement strong authentication: Use MFA methods that comply with regulatory standards. SMS two-factor authentication is widely recognized for its security.
Regular audits: Conduct regular audits to ensure ongoing compliance. This helps identify and mitigate potential security gaps.
Employee training: Offer training certificates to emphasize the importance of compliance and secure authentication practices. Educated staff can better prevent security breaches.
Fyno's approach to SMS authentication
Fyno verify
Fyno Verify is a comprehensive solution for securing online transactions and access. It uses advanced public key cryptography to ensure the integrity and confidentiality of authentication codes.
Public key cryptography: Ensures secure and encrypted communication.
Real-time verification: Provides instant verification of user identity.
Fraud detection: Prevents fraudulent activities during the authentication process.
Seamless integration with existing systems
Our product can be integrated seamlessly with your existing IT infrastructure, allowing enhanced security without significant changes. This ensures that organizations can adopt advanced security measures with minimal disruption.
Compatibility: Works with various systems and platforms.
Ease of implementation: Quick setup with minimal changes required.
Flexible API: Fyno's flexible API supports customization and smooth integration.
In fact, Fitpass has achieved 100% SMS deliverability and robust authentication through our intelligent routing and failover mechanisms. This significantly enhanced their security and user experience, providing reliable and seamless communication.
FAQs
1. What is SMS Authentication?
SMS Authentication is a security process where users receive a unique code via text message to verify their identity.
2. How secure is SMS Authentication?
It adds an extra layer of security by requiring both a password and a code sent to a mobile phone, preventing unauthorized access.
3. How does SMS Authentication work?
Users log in with their credentials, receive a unique SMS code, and enter it on the login page. The system verifies the code.
4. What are the types of One-Time Passwords (OTPs) used in SMS Authentication?
Types include Time-based OTPs (TOTP), Event-based OTPs (HOTP), Biometric OTPs, and SMS-based OTPs.
5. What are the benefits of SMS Authentication?
It offers enhanced security, user-friendliness, broad acceptance, easy implementation, and cost-effectiveness.
6. What are the security concerns with SMS Authentication?
Vulnerabilities include SMS spoofing, SIM swapping, and the lack of encryption in SMS messages.
7. What are some alternatives to SMS Authentication?
Alternatives include authenticator apps, FIDO2 security keys, biometric authentication, and email authentication.